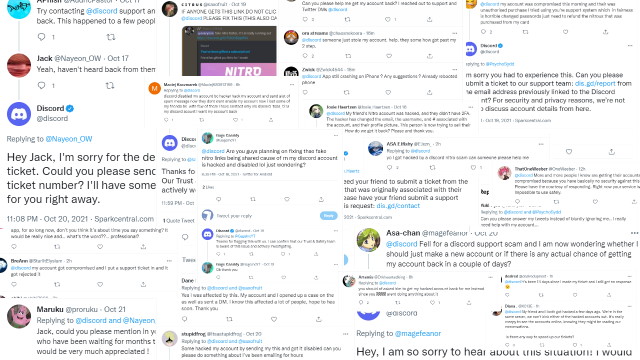
A small sample of people's pleas to Discord - from Twitter
Should you open any Discord tweet and scroll past the usual meme and good time responses, you'll see no less than a few pleas for help - even more if you look at their mentions.
So how did we get here and how does it keep getting worse - with even competent users losing their accounts and servers to hackers?
Attack vectors
Some of the common attack vectors are:
Password reuse
Password reuse is simple enough to avoid - DO NOT use the same password for multiple websites/services - else if one of them gets breached and leaked into wild, people can use the password to log into all of your other accounts.
Using an external password manager with a master password (e.g. BitWarden) can spare you of having to remember dozens of "sufficiently secure" passwords and is strongly encouraged.
Social engineering
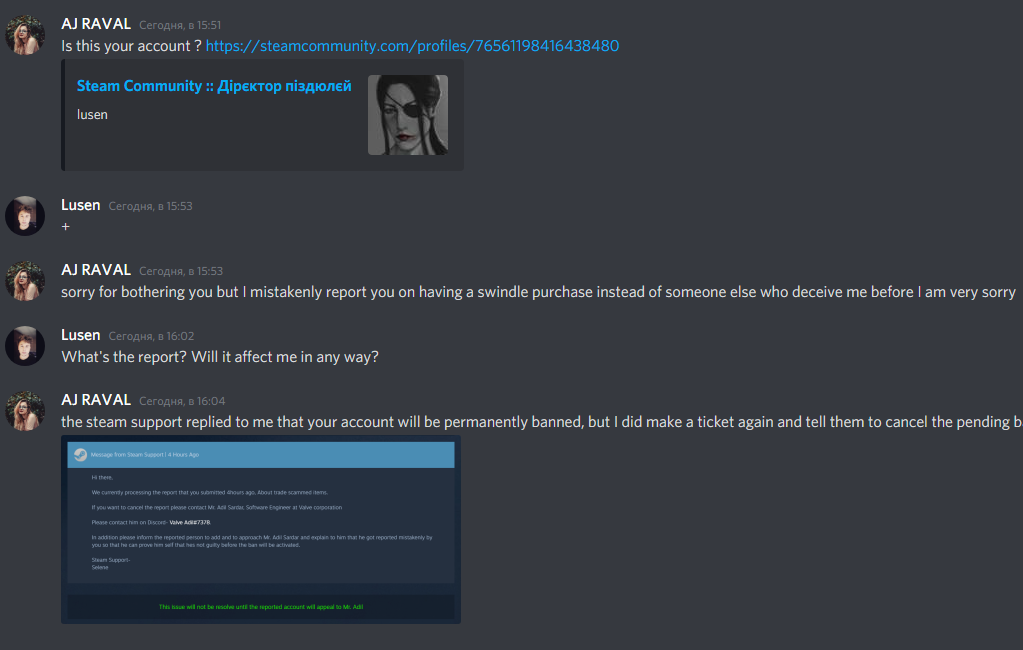
An example of social engineering attempts on Discord - a screenshot by lusenpai.
Social engineering is deceiving by pretending to be someone (in this case, commonly Discord support) to get you to do something (usually, hand over username, password, and 2FA under guise of identity verification).
Takes a little care to avoid, but, rest assured, Discord or Steam wouldn't contact you about account issues by adding you as a friend on Discord. Or by emailing you from an unofficial email. And if a friend of yours is acting sketchy, ask them to verify by messaging you elsewhere!
Phishing
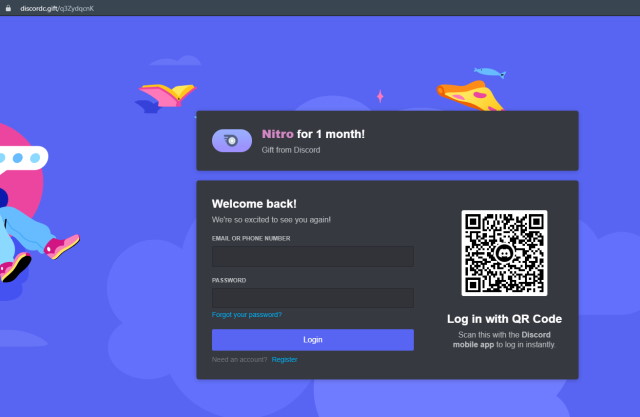
An example of a Discord phishing website - a screenshot by Mathys C.
Phishing is the process of fooling you into entering your credentials on an unrelated website, usually on premise of getting free Nitro. You have definitely seen at least a few of these as they pop up and vanish on daily basis.
Talking the obvious here, but you should never enter your credentials on unrelated websites - if a website integrates with Discord, it'll redirect you to Discord website to ask for permissions (and even then, you should triple-check the URL before entering anything).
Should you fail this little attention check, your account will be either stolen and sold (if it has a payment method attached or other value) or used to spam links to the same phishing website until Discord perma-bans it for spam.
The good news are that if you have opened a phishing site but haven't entered anything, the odds of your account being compromised are astronomically low - even lower in our modern days of Flash and PDF viewer plugins all but obliterated from browsers.
User tokens
User tokens are a little more interesting:
They are, essentially, your login session - when you log in, a token is generated. When you log out (or after a while), the token is invalidated. A token "renews" while in use. Password resets use short-lived tokens. Usual stuff.
There is a little caveat - tokens aren't bound to system nor geographically, meaning that if someone can get their hands on your token, they can access your account - wherever they are.
Discord takes basic precautions against your token being stolen from right before your eyes, but as the last window/tab of Discord closes, it has to save the token somewhere so that you don't have to re-login next time you open the app.
And thus, to steal a token, malicious application has to wait for you to exit Discord first before it can send your token off and/or get down to its dirty business. Or it might just kill the running process, that also works.
A token is enough for most operations (saving for email/password change and account deletion), but malicious applications will usually also infect the Discord installation to do a "proper" account takeover the next time you attempt to log in.
Security recommendations are foggier here - of course, "don't download malware", but malware can now be found in many places - in sketchy games you get DMs about testing, in browser extensions, in innocent-looking jam games, in software libraries with name mimicking that of more popular ones, or even what may seem like "normal" games.
2FA
At this point some of the readers might get an urge to interrupt this with "Well, you see, I have something that the common victims lack - a brain and a linked 2FA app",
And you could be right, but 2FA doesn't mean jack on Discord. Try guessing which of these actions require 2FA confirmation:
- Changing the user's password and/or email address
- Buying hundreds of dollars worth of Nitro gifts
- Irrevocably deleting server data that user owns
(any actions except for server deletion - this includes banning everyone and deleting every channel)
Answer follows ➜
None at all! 2FA is only used for email+password login and to unlink 2FA. But in practice, not even the latter - we'll get to it in a bit.
So if an app can fetch your token (which anything you download might do), it can spam itself to your friends, wreck your stuff and spend your money, while falling for a phishing site (or having your Discord install replaced with a credentials+2FA logger, mentioned above) will cost you everything.
Oh, and about unlinking 2FA... did you notice that viewing your 2FA backup codes doesn't prompt for anything? Once you're logged in, you can get rid of it.
In comparison, if you were to steal my Steam session (which is region+machine bound by the looks of it), you could play videogames, but not buy new ones (because my payment method uses 2FA) nor trade any items of remote interest (which prompts for a Steam Guard code). A VAC ban is usually the worst to come out of a Steam account hack, and support is fast to revert the email change if you have any receipts/physical codes to prove ownership.
Response
This might seem like a pretty serious issue, so what does Discord do?
- Blame you (yes, really)
- Decline to restore lost servers/channels
- If your account was used for spam, it'll be deleted - no appeals
(and no matter how many hundred dollars you've given them - good user retention)
All of this on top of week-long wait times to get a human to respond to your ticket as such.
But wait, it gets worse: you know how when you email support, they attach it to your account and you can look at it at Support website?
They do for login issues too, so a person that now has access to your account can just... go there and close your ticket. [ref].
This is the point where I'd usually reassure you that things will get better, but this had been an issue for so long that there are now "black markets" for stolen Discord tokens, and there currently aren't any promises of investigating security improvements.
Jan 2022 update: at this point around 1/6..1/4 of posts on the unofficial Discord subreddit are one of the following:
- "My account got stolen, what do I do?"
- "How long does support usually take to reply?"
(OP hasn't heard back for weeks after providing all proof they could) - "Is this real? <a screenshot of an obvious phishing link>"
Conclusions
- Use a password manager.
- Be careful about trusting people or web pages.
- Be extra careful about running executables from the web.
If you have sufficient familiarity/willingness to learn, run unfamiliar applications in a VM or isolated environment (e.g. Sandboxie) that is configured to forbid access to important directories. - If you have Discord servers that are important/dear to you, consider transferring their ownership to an account that is never used on "unsafe" machines (e.g. only on mobile devices that do not have obvious attack vectors).
- If you are an administrator of a particularly big Discord server,
you may have to eventually investigate offloading the "administrator" role onto a bot
so that the channels can't be wiped if someone gets their account compromised.
Unfortunately, Discord seems to be actively working on adding more and more bureaucracy into bot development, which can be particularly troublesome for moderation bots with plenty of permissions.
That's all..?

Viewing 2FA backup codes prompts for your password.
So it’s not nothing, but I don’t think it prompts for 2FA.
The URL to the phishing site alone is enough to make me laugh and ignore it. Guess I take common web sense for granted, none of what’s stated here really worries me. Can’t believe this old timey crap is still working so well.
The list can now be expanded with “people scanning a login QR code and approving the session [despite the screen straight up telling them what will happen] because a bot told them that this is how to prove that they’re human”.
You might be “shocked” to know that auth tokens will never expire.
Even if a new one is generated by a login, an old one will continue to work.
The only way to invalidate (all) old tokens is to change your password.
That does have to work like that to allow multiple sessions (e.g. from PC and from mobile), but, unlike most other services, Discord doesn’t currently have a way to view the list of your sessions and their locations.
More shocking is that logging out doesn’t invalidate the session token – the only action that invalidates a token is resetting your password, which invalidates *all* tokens.